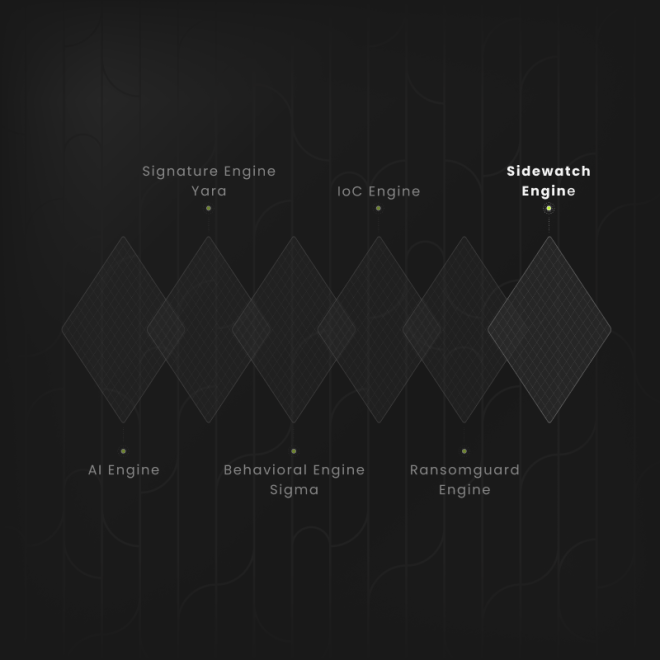
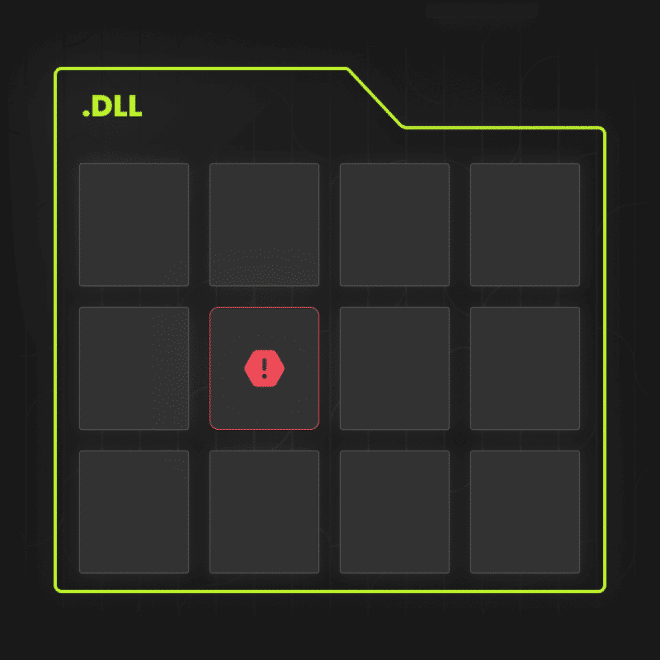
The Sidewatch engine detects attacks using DLL Sideloading techniques.
DLL Sideloading is a technique frequently used for advanced attacks and cybercrime. It involves using a legitimate executable to load a malicious library.
Attackers take advantage of the executable vulnerabilities and the fact that they are considered as reliable or signed, and therefore less monitored, to execute malicious payloads without being detected by cybersecurity tools.
The malicious payload may be embedded in a legitimate DLL, and may be encrypted, compressed, or obfuscated to evade detection.
To prevent this, the Sidewatch engine observes the behavior and activity of .dll files.