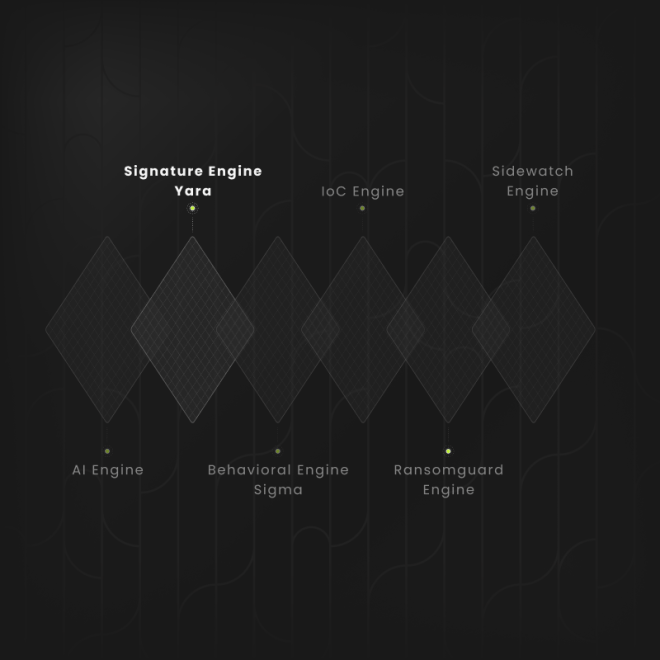
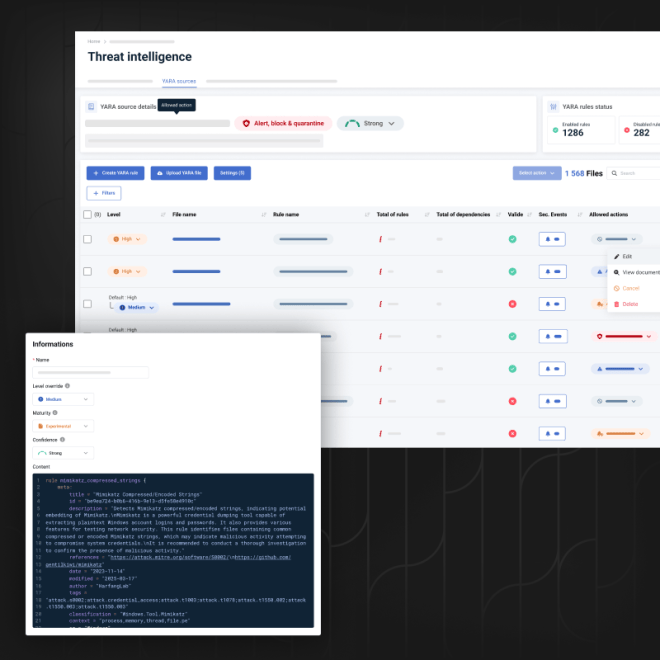
The Signatures Engine features rules designed to detect attackers’ tools, and can be configured to scan executables as soon as they are written to disk for Windows, MacOS, and Linux agents.
It detects known threats such as CobaltStrike, Bruteratel, Mimikatz, Metasploit, Sliver, and more.