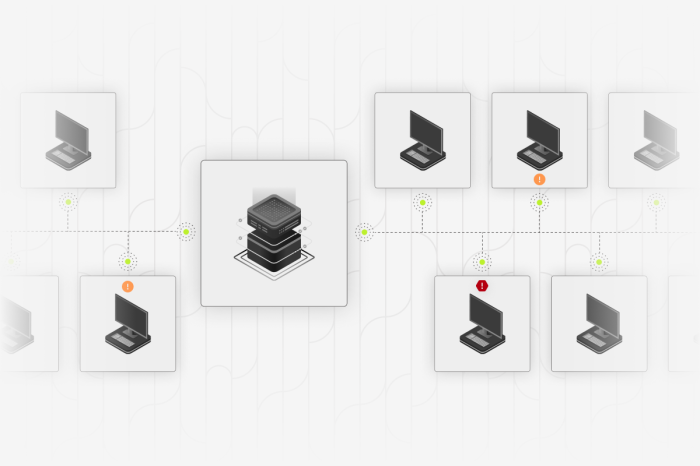
Thanks to the HarfangLab agent deployed on your workstations and servers, all endpoints can be mapped and associated with the network they are on without the need to install a probe.
HarfangLab uses the data collected on each endpoint by the agents to detect the presence of IT assets that are not protected by HarfangLab.
The endpoints send requests, or network packets, and based on the responses, the EDR detects the presence of unknown devices and can infer their specific characteristics (device type, OS, version, etc.).