📑
The aim of a FIM is to detect any alteration or corruption likely to indicate a cyberattack via file systems, directories, databases, network equipment, operating system assts, or software applications.
FIM compares the current state of files with a trusted reference to identify unauthorized or unexpected modifications. This verification of file integrity can be carried out reactively via audits or proactively using predefined rules.
A FIM tool generates alerts to prevent modifications to critical files concerning identification information, content, rights, security parameters, size, or hash.
Implementing FIM is important for ensuring the security of information systems, as it enables early detection of signs of compromise, speeds up incident response, and ensures compliance with current laws and regulations, such as the PCI DSS standard in banking and finance, HIPAA for the healthcare sector, GDPR, ISO 27001, or the recommendations of NIST or SANS Critical Security Control.
In short, a File Integrity Monitoring solution aims to:
-
ensure compliance of the information system protection
-
ensure the integrity of critical files and application configurations
-
detect vulnerabilities arising from modifications to critical files
-
identify cyberattacks targeting data security
-
precisely trace modifications to critical files to speed up incident response
Let’s take a closer look at the benefits of File Integrity Monitoring with a few use cases.
The perks of File Integrity Monitoring
Here are 3 examples of the benefits of File Integrity Monitoring.
FIM for compliance
As part of an audit, the FIM can be used to prove that the tools and resources are in place to warn security teams of fraudulent modifications to sensitive data, so that they can react accordingly. Furthermore, in the event of an incident, FIM provides a history of file modifications, and we’ll see how correlating this information with EDR data can provide a detailed report.
FIM to protect against cyberattacks
FIM enables file modifications to be tracked, so that incidents involving both external attacks and internal malicious acts can be avoided.
Administrators can be alerted, react in time, and take appropriate investigative action. Investigations can go even faster if the data is correlated with EDR telemetry – a point we’ll also look at a little later.
FIM for monitoring the configuration of critical applications
The configuration of applications can be monitored with FIM to ensure that they are not subject to unforeseen or unintentional changes that could lead to vulnerabilities or service interruptions.
In short, FIM helps ensure compliance and, more broadly as its name suggests, it helps ensure file integrity to protect an information system.
And if a security incident occurs? Let’s take a look at the advantages of combining FIM and EDR to speed up investigations.
FIM & EDR: for faster, more efficient investigations
A standalone FIM generates alerts following modifications made to a computer file, but in most cases, it gives little information on the details of who modified what and how.
The ability to correlate EDR telemetry with FIM alerts makes investigations much more effective and provides complete and rapidly exploitable information, which is essential in the event of a cyberattack.
Thanks to FIM alerts and EDR telemetry, analysts can identify precisely which files have been modified and how, so they can dig deeper into the attack path.
In practice, how does HarfangLab FIM work?
HarfangLab FIM
HarfangLab includes a FIM in its EDR license. It provides data and alerts on critical file modifications.
These alerts can be configured on file content and/or metadata, with the possibility of defining rules for:
- selecting the information to be retrieved
- defining the frequency of checks
- creating exclusions to limit false positives
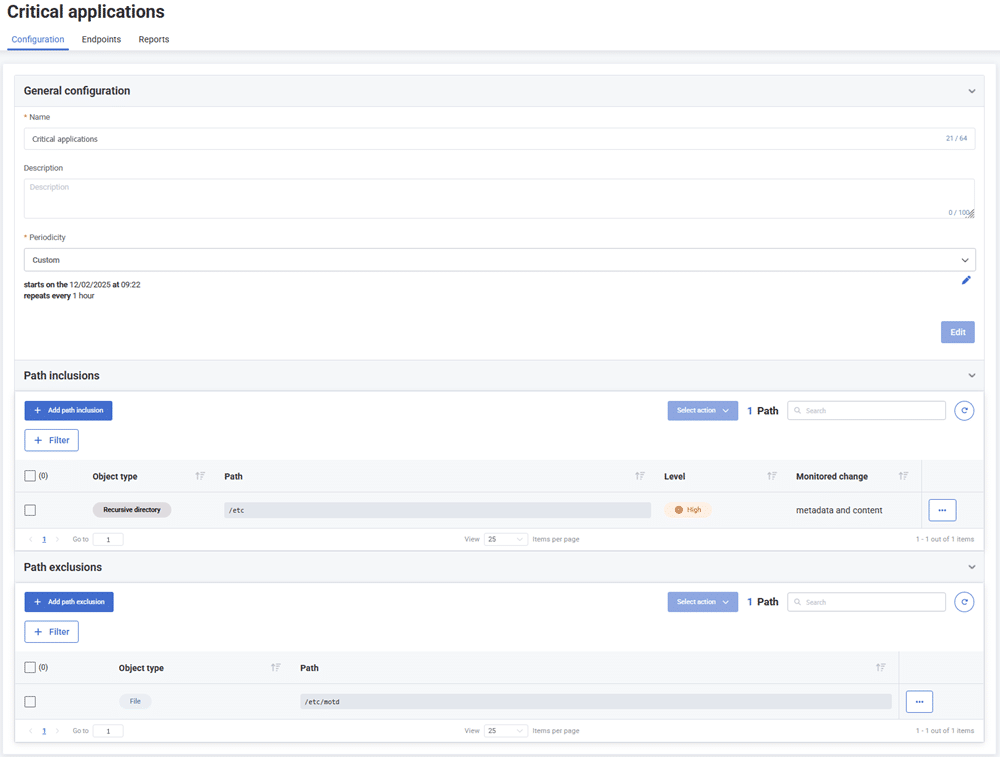
Based on these settings, the EDR generates reports on modified files, where analysts can identify possible security incidents and take the necessary actions.
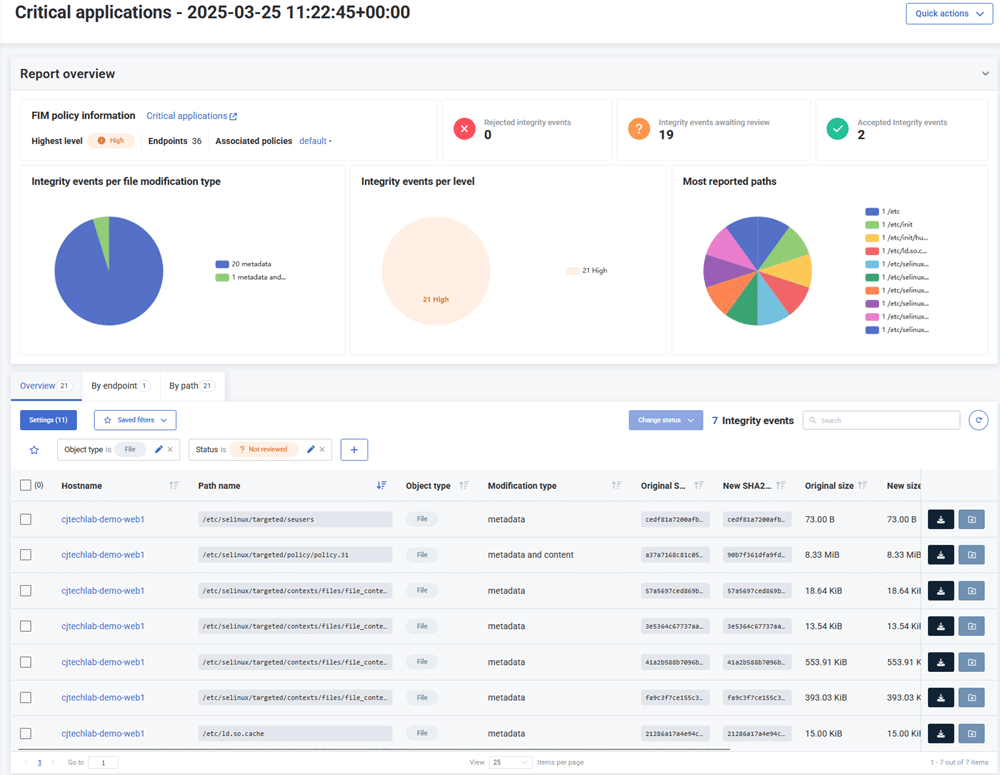
Thanks to the EDR’s integrated FIM functionality, analysts can much more easily link critical file modifications with telemetry data from an endpoint. This is a major advantage over standalone FIM tools, which cannot correlate file modifications with activity on an endpoint.
Find out more about our features,
discover our plans:





