EDR & MITRE ATT&CK

What is MITRE ATT&CK, how does an EDR evaluation work, what are the evaluation criteria, who uses it, and what does it mean for experts and vendors of cybersecurity solutions?
Let’s take a look at the framework, the techniques and tactics evaluated, and HarfangLab’s EDR assessment.
What is MITRE ATT&CK?
MITRE ATT&CK is a reference framework for evaluating detection capabilities, threat hunting, risk management, Threat Intelligence… Born in 2013, it is an alternative to the CyberKill Chain developed by Lockheed Martin. This framework evolves regularly to adapt to the cyber context. MITRE ATT&CK has 3 components to assess detection on:
- workstations and servers in Windows, Mac, Linux and Cloud environments (Enterprise ATT&CK);
- mobile for iOS and Android operating systems (Mobile ATT&CK);
- industrial networks (ICS ATT&CK).
Tactics and techniques assessed by MITRE
MITRE ATT&CK has 14 tactics, each with its own technical objectives. The tactics are as follows:
- Reconnaissance
- Resource development
- Initial access
- Execution
- Persistance
- Privilege escalation
- Defense evasion
- Credential access
- Discovery
- Lateral movement
- Collection
- Command and control
- Exfiltration
Within these tactics, techniques are the methods used by attackers. They will depend on their objectives, their skills, the configuration of the intended target… MITRE ATT&CK includes almost 200, and nearly 400 sub-techniques.
Who uses MITRE ATT&CK?
The MITRE ATT&CK framework is useful for a wide range of cybersecurity players.
CISOs and CIOs, as well as MSSPs and SOC Managers, can use it as a decision-making tool to assess the performance and relevance of solutions on the market.
Cyber Threat Intelligence (CTI) researchers can use it to categorize threats, and correlate the Techniques, Tactics and Procedures (TTPs) of different attacker groups.
It is also useful for Red Teams to facilitate the classification of vulnerabilities identified in an Information System.
Finally, cybersecurity solution suppliers can use it to assess their detection capabilities with a view to improving them, to meet market needs and to monitor the evolution of the threat.
In addition to its framework, MITRE ATT&CK also offers the MITRE ATT&CK evaluation grid. It is also a framework for presenting the techniques and tactics their solutions cover.
Detection and protection: HarfangLab EDR MITRE ATT&CK Evaluations
2023: first participation in MITRE ATT&CK to evaluate detection
The evaluations involved emulating Turla, an attacker group known for its targeted intrusions and stealth.
Turla executes targeted campaigns aimed at exfiltrating sensitive information from Linux and Windows infrastructures. In practice, once it has established itself, Turla persists with a minimal footprint, thanks to memory or kernel implants.

In 2023, HarfangLab EDR detected:
- 100% attacks steps (19/19)
- 100% tactics (11/11)
- 98% real time (3 delays)
2024: 100% detection and 99% accuracy
The 2024 edition of the MITRE was marked by several new features, including evaluation of detection on macOS and ransomware attack scenarios:
- APT on macOS with a simulated attack that could be carried out by a North Korean actor
- Ransomware on Windows and Linux with simulated attacks by the CL0P and LockBit groups
In addition to its detection capabilities, HarfangLab also evaluated its protection and false positives:
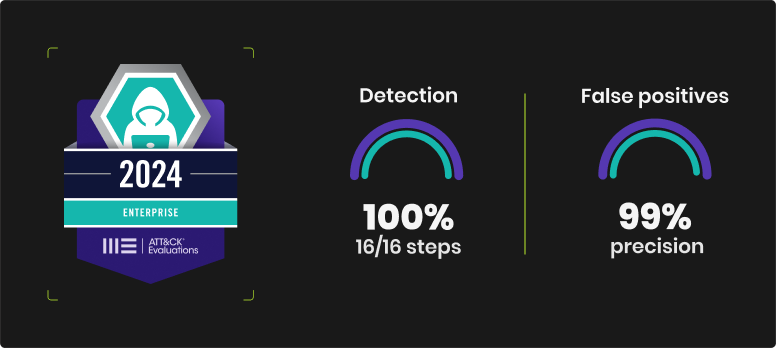
- 100% of attacks detected
- 8 steps immediately blocked, interrupting the attack at the first action of the attackers (i.e. 30% more effective than the participants’ average)
- Accuracy rate of 99% in false positives evaluation
MITRE Evaluations: test scenarios
The evaluation includes several steps.
First, test scenarios are played out.
Typically, these scenarios begin with an initial compromise and end with the attacker’s trying to achieve their objectives.
Depending on the type of attack emulated (ransomware, APT…), the steps can vary a lot. They may, for example, include: initial compromise, discovery and privileges escalation, lateral movement, compromise or collection of data…
A final step is to test the EDR’s protection capabilities by checking whether or not it is capable of blocking attacks.
To run these tests, a team made up of a project manager, the CTI team and DevOps support, back-end and front-end, mobilized over 3 to 4 days to deal with the attacks launched by the MITRE Red Team, and answer questions on EDR detection proofs (you can take a look in 2023 and 2024 backstage).
Within each stage, there are sub-stages for which MITRE ATT&CK assigns a detection classification from the most precise to the least specific: technical, tactical, general detection, telemetry. This classification is used to assess how well the tool detected the event.
Following the test days, the results are then consolidated by MITRE ATT&CK for all participants, for public release.
This demanding test is also internationally recognized, providing a benchmark for experts and decision-makers in the cybersecurity sector, and, through its high standards, helping to raise the bar for all players.
Want to know more about our EDR?
Find out how HarfangLab protects your endpoints:
![[Webinar] MITRE 2024 Results](https://hubspot-no-cache-eu1-prod.s3.amazonaws.com/cta/default/25847055/interactive-237880147136.png)
