The antivirus analyzes file signatures and characteristics (extension, header, etc.), regardless of the operating system (Windows, MacOS, Linux) to determine whether the file is a threat or legitimate.
Depending on the type of file, it is analyzed as soon as it is placed on the disk or at runtime.
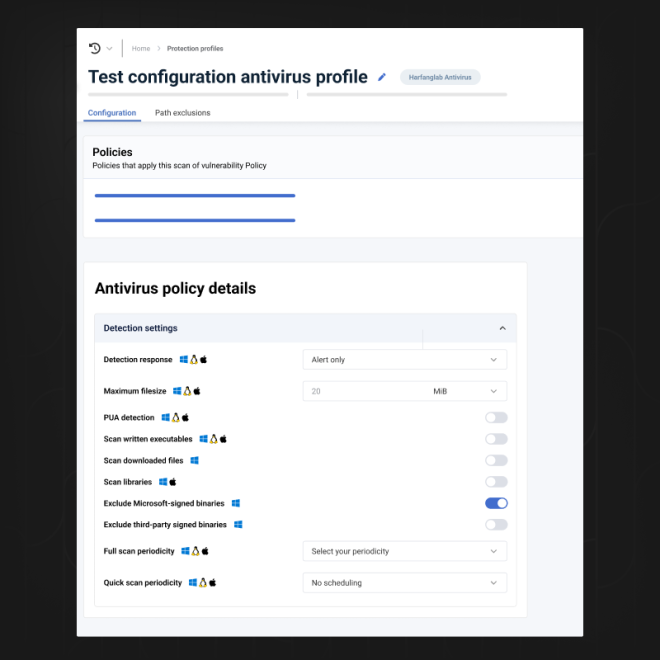
The antivirus can then block or even quarantine these files if the signature corresponds to a known threat in its database. More precisely, each file, regardless of its appearance (size, extension, etc.), is subject to a multi-stage process involving heuristics and behavioral analysis in addition to static and traditional signature-based analysis.
Analysis includes suspicious data elements, as well as signature and exploit detection, for immediate virus isolation and neutralization. Files are executed and, if necessary, monitored and analyzed in a closed virtual environment.
External devices and USB sticks can also be scanned.