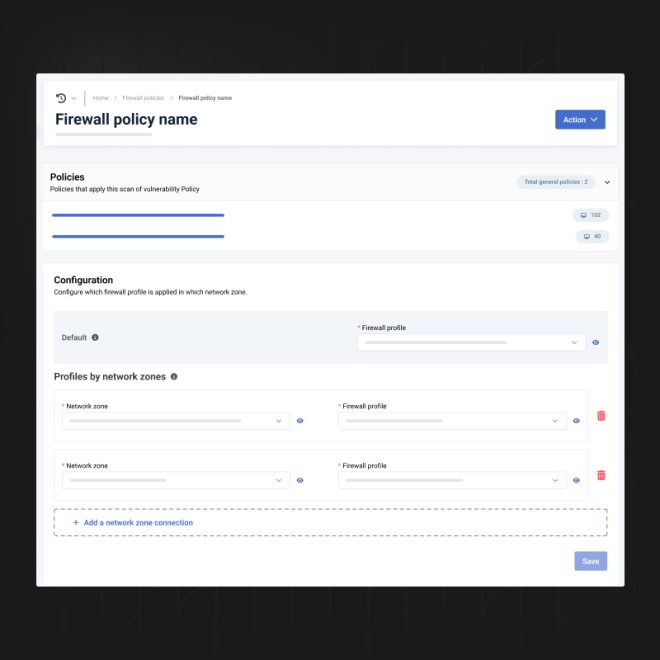
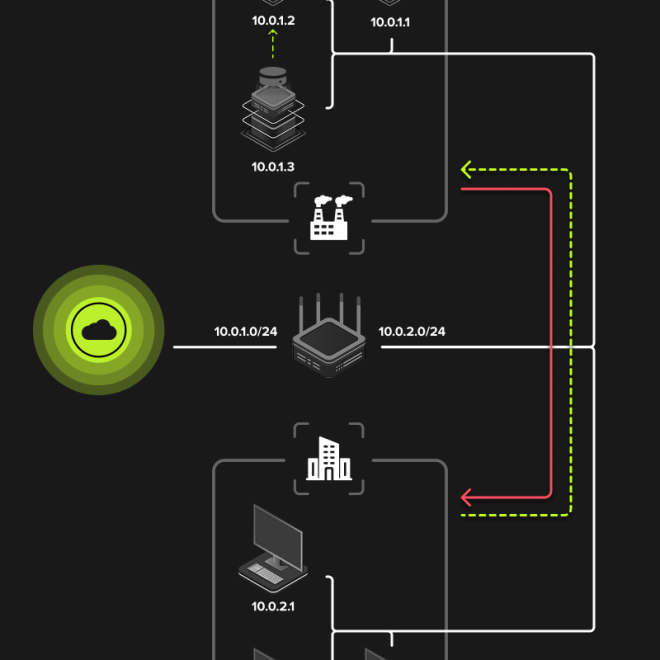
The firewall policies enable a firewall profile to be associated with endpoints, i.e. a set of filtering rules applied to network connections, based on:
- Network protocol (IPv4 / IPv6 and/or TCP / UDP / ICMP),
- Direction (inbound, outbound, or both),
- Local host, i.e. protected endpoint (single IP address / range / CIDR, port, and/or application),
- Remote host, i.e. the remote endpoint concerned by the connection with the protected endpoint (single IP address / range / CIDR, or FQDN and/or port).
For cases that require the dynamic application of different firewall profiles within a complex network context within a company (e.g. on-the-move endpoints, server simultaneously connected to several networks), HarfangLab’s EPP firewall lets you define network zones based on various parameters such as network interface type, associated IP address, and choose which profile to apply in which network zone via the firewall policy.
These firewall policies are then associated with endpoint policies, unifying all configuration elements in the console.
Incoming and outgoing network connections are filtered using rules configured and administered directly from the HarfangLab console.