Thanks to its single lightweight agent, HarfangLab transforms each endpoint into a watchdog for the entire IT infrastructure, with no impact on workstation or server performance.
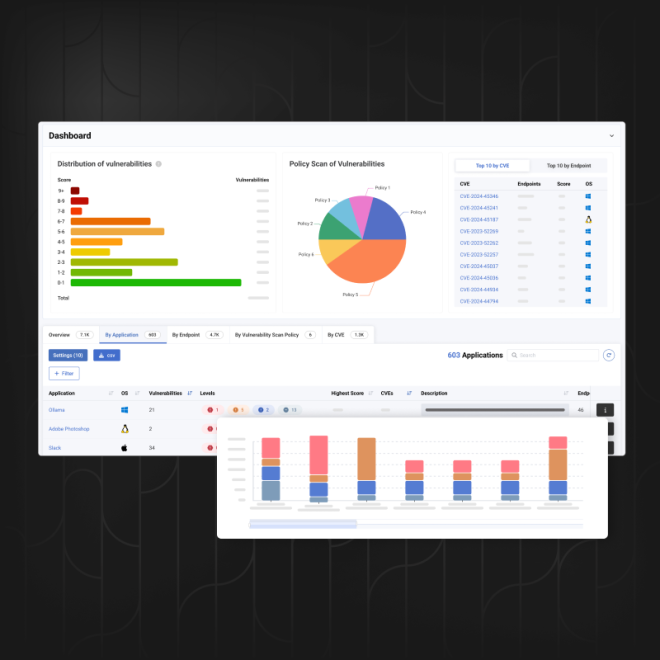
Vulnerability Assessment does not require heavy and time-consuming manual scans, nor does it require opening ports or permissions… because the agent installed on each endpoint automatically detects vulnerabilities.