📑
Information system mapping: Definition
The aim of mapping is to represent an organization’s information system and its connections with the outside world. It provides insights into all components of the information system and gives a clearer picture of what is involved.
This mapping is essential for controlling, protecting, defending, and ensuring resilience in the event of a cyberattack.
It may concern IT infrastructure, applications, network connections, processes, resources involved in information system management… It is this diversity of information system viewpoints that enables effective monitoring, and optimal reaction time in the event of a security event.
Although there is no single reference, mapping is as much a part of ANSSI’s “Information Hygiene Guide” as it is of the French Military Programming Law, or NIS 1 and 2.
Nevertheless, it can be a thorn in the side of security organizations. Mapping can reveal technical debt or obsolete architectures that are ill-suited to security challenges. It can also reveal gaps in documentation, loopholes, and even actions that have slipped under the radar.
What are the different tools and methodologies available to tackle mapping effectively?
Information system mapping tools: advantages and limitations
Mapping can cover all aspects of an information system. It can also be carried out in different ways, depending on the needs of an organization, the resources available, and the complexity of the technical infrastructure.
To make it a real decision-making tool, it is important to bear in mind that mapping should not be seen as a one-shot project. It’s a long-term process that requires regular follow-up.
For a less complex environment, a static, manually-updated map or a Configuration Management Database (CMDB), may be appropriate.
On the other hand, the more complex the IT environment and the more frequent the updates, the more automation and centralized management will be key to ensuring that the mapping remains relevant.
As we will see, according to a summary produced by Cyberun (#36 about mapping), each solution has its advantages and limitations. What are they?
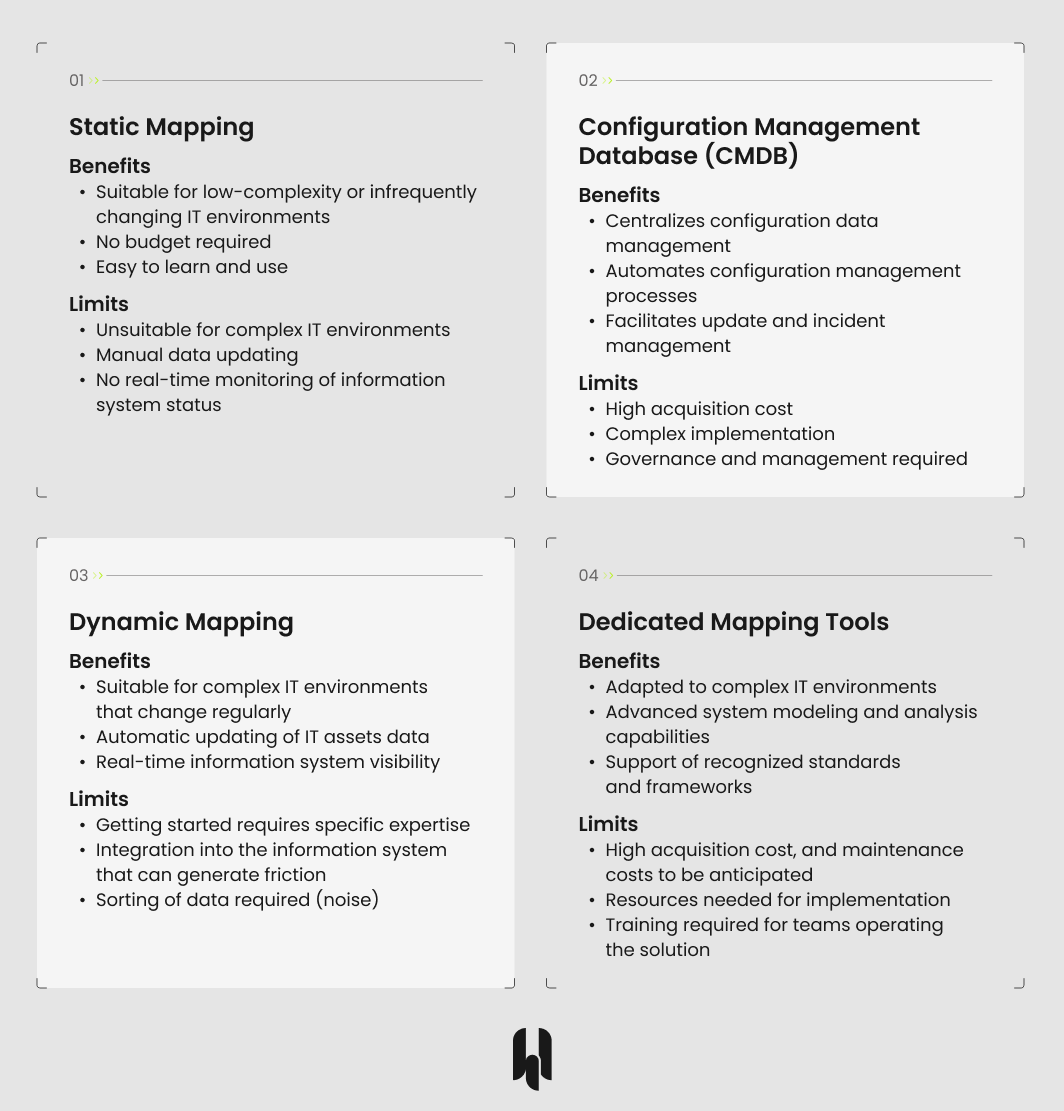
Static Mapping
This is suitable for less complex environments and relies on easy-to-use office tools such as spreadsheets with data and graphics. Updating is manual.
Perks of Static Mapping
- Suitable for low-complexity or infrequently changing IT environments
- No budget required
- Easy to learn and use
Limits of Static Mapping
- Unsuitable for complex IT environments
- Manual updating of information
- No real-time monitoring of information system status
Configuration Management Database (CMDB)
The CMDB is a database containing all the information about the hardware and software components of an information system, and the links between these components. It can be used to generate detailed mappings and collect metrics on the use and performance of IT components.
Perks of CMDB
- Centralizes configuration data management
- Automates configuration management processes
- Facilitates update and incident management
Limits of CMDB
- High acquisition cost
- Complex implementation
- Governance and management required
Dynamic Mapping
Dynamically mapping an information system is highly recommended for evolving IT environments. This allows teams to automate the integration of a large amount of data for enhanced monitoring. Beware, however, that some information cannot be automated, such as the criticality of certain applications, or links between processes and applications…
Perks of Dynamic Mapping
- Suitable for complex IT environments that change regularly
- Automatic updating of IT asset data
- Real-time information system overview
Limits of Dynamic Mapping
- Getting started requires specific expertise
- Integration into the information system, which can generate friction
- Data cleansing required (noise)
Dedicated Mapping Tools
In addition to tools such as CMDBs, there are advanced solutions dedicated to managing information system mappings. Particularly well-suited to complex IT environments, these solutions include functions for modeling and analyzing IT assets.
Perks of Dedicated Mapping Tools
- Adapted to complex IT environments
- Advanced system modeling and analysis capabilities
- Support for recognized standards and frameworks
Limits of Dedicated Mapping Tools
- Higher acquisition cost, and maintenance costs to be anticipated
- Resources required for implementation
- Training required for operating the solution
Overview from Cyberun #36 “Cartographie”, available for free
Mapping an information system: the expert’s tip
“Mapping an information system is essential for good IT hygiene, and a valuable tool for identifying and remedying vulnerabilities in applications.
It also speeds up investigations, because in the event of an attack, mapping enables teams to locate the attacker’s entry point and the affected business services much more quickly.
Sure, analysts might receive an alert about suspicious activity on a server, but without knowing which applications are hosted there, it is impossible to estimate the criticality of the alert. Mapping provides immediate access to this information.”
Rémi Pointel, Pre-Sales Engineer – HarfangLab
And beyond mapping, what are the keys
to greater cyber resilience?





