📑
Managing your attack surface is crucial for the security of an information system. A Gartner study carried out in 2024 indicates that 80% of ransomware attacks originated from unsecured equipment, 30% from misconfiguration, and 20% from unpatched vulnerabilities.
However, this issue remains a major challenge for security teams. Assets and applications are becoming increasingly numerous, and in the event of an incident, remediation requires significant efforts in terms of resources and organization.
Since anticipation is key when it comes to cybersecurity, switching from a reactive approach to a proactive one can make all the difference! HarfangLab offers an Attack Surface Management solution called “Scout” that includes the tools you need to assess your security level, detect vulnerabilities, and anticipate threats while simplifying your cybersecurity stack and helping you comply with legal requirements (ISO 27001, NIS2, DORA, GDPR, etc.).
Let’s take a closer look at the features in Scout.
Attack Surface Management features
Attack surface management is defined as the ability to identify weaknesses in an information system’s protection: vulnerabilities, obsolete OS versions, unpatched applications, unprotected endpoints, and so on. These are all entry points or flaws that attackers will inevitably seek to exploit.
Vulnerability Assessment
The Vulnerability Assessment feature included in Scout lists and prioritizes Common Vulnerabilities and Exposures (CVEs) and manages patch deployment across OSes and applications installed on the information system.
More specifically, the HarfangLab agent identifies the versions of applications and operating systems present on workstations and servers in the IT infrastructure and compares them with the National Institute of Standards and Technology (NIST) vulnerability library. If a vulnerability is identified, it is indicated in the console.
This vulnerability detection is performed continuously by the HarfangLab agent installed on your endpoints, eliminating the need for network scans, which are a heavy, instrusive, and time-consuming.
Thanks to the Vulnerability Assessment feature, cyber analysts have centralized access to all data collected by the platform (Attack Surface Management, EDR, and EPP) to easily correlate it and speed up investigations in the event of a security incident.
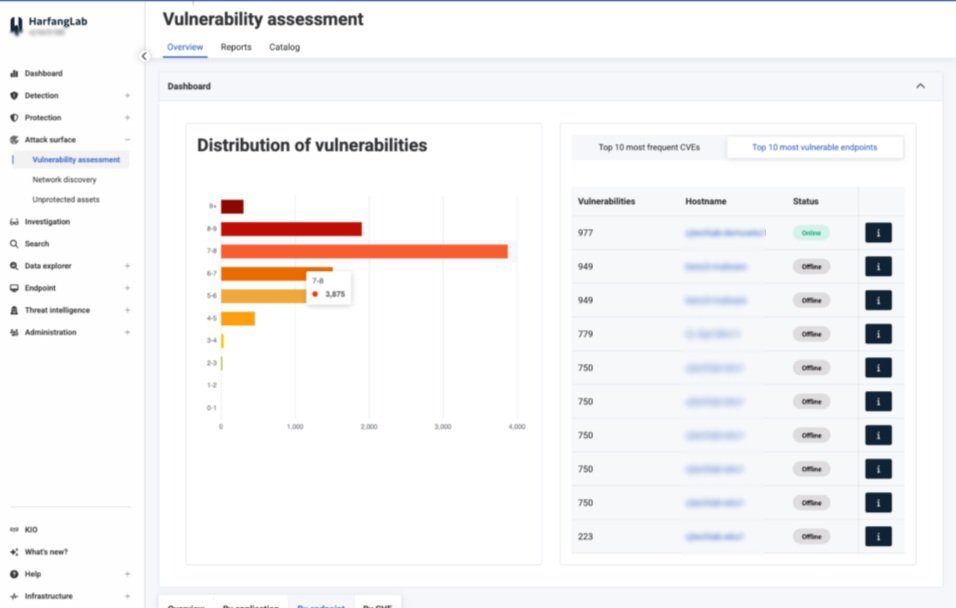
The HarfangLab console provides a view of all installed applications (including version and update date) and enables you to identify which endpoints are equipped with vulnerable versions based on the CVE number so that you can patch them.
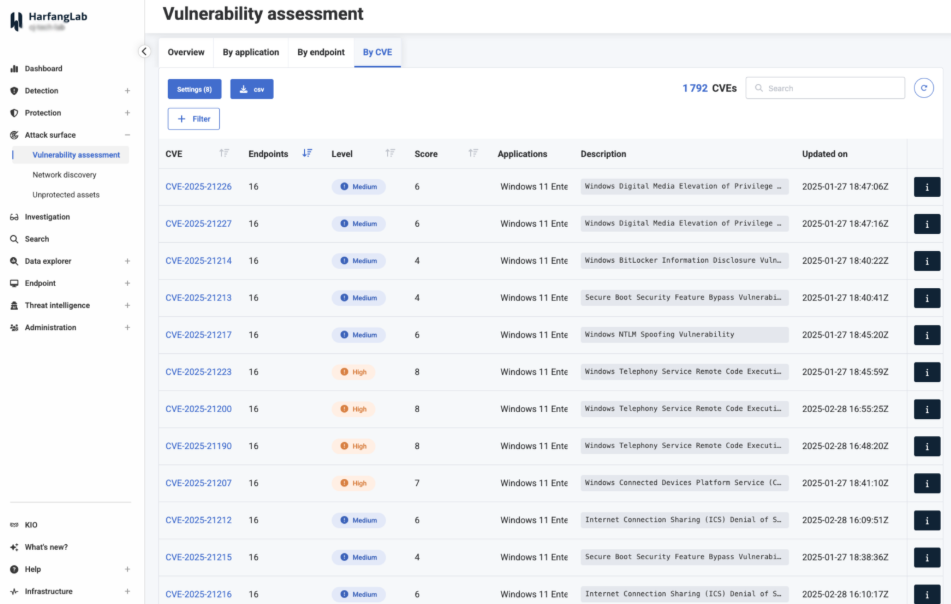
The console also displays a list of all vulnerabilities detected on a computer network, then compiles a list of endpoints with the highest number of vulnerabilities, as well as the most vulnerable applications by ranking them according to the criticality level of vulnerabilities so that your team can prioritize patches.
The view is provided in real time, and a record is also accessible to track improvements in security posture over time. Following a security incident, Vulnerability Assessment identifies whether the vulnerability was already present at the time of the attack, and if this vulnerability could have been the root cause.
Shadow IT Discovery
The Shadow IT Discovery feature uses network detection to compile a list of unprotected endpoints. The agent deployed on endpoints sends network probes to identify unprotected devices on the network. Unprotected devices can then be flagged so that your teams can take the necessary measures (protection, restriction of certain access, etc.).
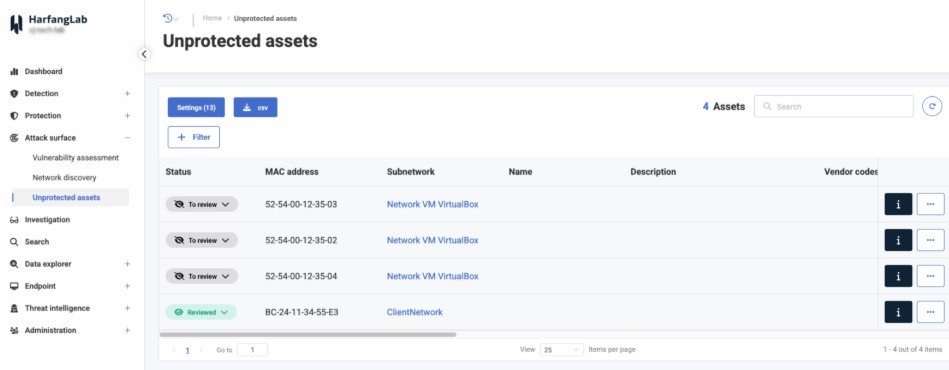
To limit noise, the Shadow IT Discovery feature provides options to include or exclude networks — for example: home networks can be automatically excluded from the scan for information system users working remotely.
Identify your vulnerabilities and take the right security measures
Attack Surface Management solutions automate preventive actions against cyber threats and enable faster, more effective remediation. In other words, Scout facilitates proactive risk management!
In terms of integration, the single agent is designed to be easily deployed in an existing infrastructure and to consume minimal resources on endpoints. And since only a single deployment is required, organizations can optimize human, material, and budgetary resources.
What about Attack Surface Management in an On-Premises environment?
Scout is also available for On-Premises and Air-gapped environments. As with CTI rules, the CVE list can be updated via a secure feed, or in cases where no feed can be opened, by importing via physical media.
Discover all that Scout can do,
starting with our live demo replay: