📑
Who are the threat actors, how has the threat changed, and what are the future trends in ransomware? Above all, how can you protect yourself?
We discuss this with Léna Jakubowicz, Presales Lead at HarfangLab.
The evolution of ransomware
From the 2020s onwards, ransomware became more sophisticated, with attacks such as those carried out via Maze or REvil, both involving double extortion and data leaks.
Today, Artificial Intelligence dramatically boosts the capabilities of attackers targeting critical infrastructure and carrying out attacks without using files.
In just one year between 2023 and 2024, ransomware underwent major changes that are set to continue, including:
- The shift from massive, low-impact attacks to much more targeted attacks involving extortion and data theft, with a multiplied impact
- An 11% increase — and this volume of attacks could reach 1 ransomware attack worldwide every 2 seconds by 2031
- An average cost per company to recover from ransomware of $3.58 million — which could total $265 billion by 2031
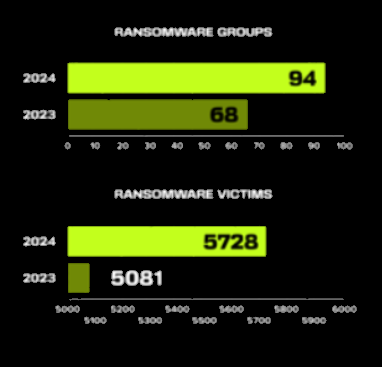
- The number of active groups has also increased (+38%), as has the number of victims (+12%)
Speaking of ransomware groups, which ones claimed the most victims in 2024?
The most active ransomware groups
LockBit, RansomHub Play, and Akira were the most active groups in 2024. For most of these groups, except LockBit, the number of victims increased between 2023 and 2024:
- RansomHub: 611 (appeared in 2024)
- LockBit: 1,041 to 494 (-52%)
- Play: 318 to 366 (+15%)
- Akira: 163 to 315 (+93%)
- Hunters: 25 to 235 (+840%)
Focus on RansomHub and LockBit
These groups develop genuine “product” approaches, including branding, repositioning operations, targeted actions, and more. They are structured and resilient criminal organizations, far removed from isolated hackers.
RansomHub
This group appeared in February 2024. It is a RaaS platform with a classic extortion site.
RansomHub may have links to BlackCat/ALPHV, and stands out for its willingness to spare certain victims, particularly in the healthcare sector (but it is also capable of pretending to spare them).
The group targets organizations in several countries, excluding certain territories such as the former USSR, North Korea, and Cuba, which allows us to make a more accurate guess about its geographical origin.
LockBit 3.0
Since 2022, the RaaS platform with the LockBit extortion site has established itself as a “brand” in the ransomware sector.
The group is believed to have historical links to Russia, but its structure is unclear. The slowdown could be linked to recent police operations or an ongoing reconstruction (LockBit 4.0).
Multiple extortions, RaaS… ransomware trends
Beyond generating revenue for active groups, ransomware has become a political weapon. Specifically, the war in Ukraine has intensified waves of pro-Russian attacks targeting Europe and the United States, and attacks between Iran and the United States have multiplied amid the conflict in the Middle East.
Ransomware has moved beyond the technological sphere to become a weapon of economic and psychological warfare.
Let’s take a closer look at recent ransomware practices.
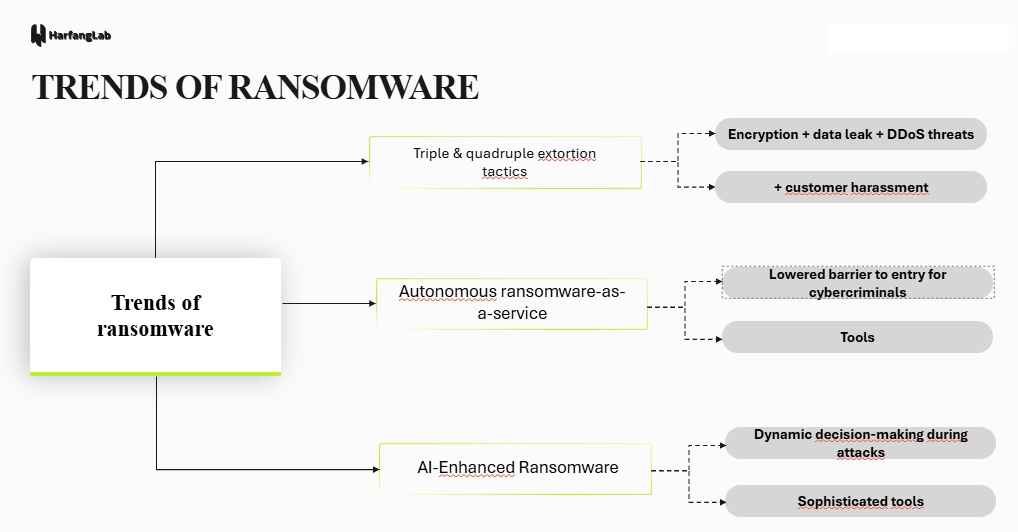
Ransomware: from extortion to triple or even quadruple extortion
Triple extortion has become standard practice, with examples including:
- Encryption
- Data theft
- Pressure on third parties (customers, partners) or threats of DDoS attacks or data resale (e.g., BlackCkat launched an attack on public servers and demanded $2.5 million from the victim)
Quadruple extortion is emerging with subsequent harassment, turning the IT attack into a communication, reputation, and governance crisis. The pressure is psychological, operational, and media-oriented.
This process is illustrated by the attack carried out in June 2024 against Kadokawa, a Japanese media group that publishes the Niconico video sharing platform. Kadokawa was targeted by the BlackSuit group (linked to Russia), which proceeded as follows:
- Encryption of systems and ransom demand
- Theft of 1.5 TB of data and threat of publication
- Pressure on third parties with public announcement of the attack
- Publication of personal data of users and partners
The Sarcoma group also carried out a ransomware attack with quadruple extortion by contacting its victim’s customers on LinkedIn using AI-generated messages.
Another notable change in ransomware is the theft of unencrypted data. Some groups, such as BianLian, are now focusing on data theft or extortion to avoid detection. In this vein, the exploitation of the MOVEit transfer solution vulnerability, among others by the Cl0p group, has claimed more than 60 million victims.
Social engineering, a technique that never fails
While attackers are increasingly turning to artificial intelligence, old tricks are still the best tricks. In other words, even with the help of AI, social engineering remains as popular as it is effective.
This was demonstrated by DarkAngels’ attack on a European energy company. The group cloned the voices of company decision-makers to encourage employees to make fraudulent payments, leading to a record $75 million heist.
In conclusion, despite the sophistication of attack techniques, some basic methods are still in use and have a catastrophic impact.
Ransomware and AI automation
Let’s return to the case of the FunkSec group, which used AI to automate certain tasks during its attack.
The group used machine learning to analyze the targeted information system network, which enabled it to identify high-value assets. In addition, AI also helped the group pause encryption during scans of the victim organization’s security solutions so as not to be detected.
The industrialization of ransomware
Ransomware may be perceived as malware, but today it goes much further: it is a business model, a structured criminal organization, with its developers, affiliates, distribution channels, tools… and now, its AI tools. Artificial intelligence is now at the heart of every stage of the attack cycle!
The development of ransomware
Viral payloads are increasingly customizable with AI-powered obfuscation capabilities, adaptive encryption, and evasion techniques via automatically updated code to avoid detection.
Recruitment of affiliates
On Telegram or forums, ready-to-use kits are offered by attacker groups, including pre-built social engineering tools tailored to the language and profile of the target. These tools enable malicious groups to recruit larger numbers of low-skilled affiliates.
Ransomware-as-a-Service: infrastructure and support
Attacker groups provide their affiliates with turnkey dashboards, payment portals, and automated attack guides. These AI-driven playbooks allow actions to be adapted to each target environment.
Execution of the ransomware attack
Fileless techniques (as seen previously), automated lateral movements, and hyper-targeted attacks driven by network data are now part of the arsenal of these malicious groups. In addition, AI enables real-time, adaptive decision-making, such as suspending encryption if an antivirus scan is detected.
Revenues are then shared between the operator and the affiliate, as in a franchise model.
The expert’s view
“We need to understand that ransomware in 2025 is no longer just a booby-trapped file sent at random. It’s rather an industrial operation driven by automation and amplified by AI.
For structured groups of attackers, each step is optimized to move faster, strike harder, and more easily bypass defenses.”
Léna Jakubowicz, Presales Lead – HarfangLab
In short, ransomware is constantly mutating, with increasingly severe impacts and sophisticated techniques, leveraging an ever-growing number of recruits. Faced with this situation, compounded by geopolitical tensions, how can we protect ourselves?
How to fight and protect your workspace against ransomware
More than tools, the primary weapon of an effective SOC against ransomware is information and intelligence about the threat: knowing what to expect and how attackers operate. Detection and protection tools must be inspired by this intelligence.
To this end, HarfangLab relies on powerful standards, continuous updates, and heuristic engines.
Sigma for behavior detection
Sigma is an open-source standard that allows you to write behavior detection rules based on system events, such as Windows logs.
These rules can detect massive access to shadow copies or backups deletion.
On the HarfangLab platform, they can be modified, shared, and easily added into the EDR.
YARA for signature detection
YARA works like a DNA fingerprint detector and can identify characteristic traces in memory or files, particularly to detect known ransomware. For example, through the presence of specific strings in a LockBit payload, or the use of a known obfuscated packer.
The advantage of YARA is that it acts at startup or during execution, enabling teams to intercept a binary before it has time to launch encryption.
Ransomguard, the engine dedicated to ransomware detection
HarfangLab includes an engine dedicated to identifying ransomware based on behavioral analysis, which relies on complementary methods.
Canary file storage
This method involves scattering decoy files across endpoints. Any attempt to encrypt, modify, or delete these Canary files immediately triggers an alert which, depending on the rules defined, can automatically block the process responsible.
This is a simple and effective method that allows for rapid detection of active ransomware, regardless of its name or family.
Behavioral analysis of the file system
This method involves continuously monitoring file system activity based on the following criteria:
- Modification speed (a process that writes or renames an abnormally high number of files over a given period of time is considered suspicious),
- Variety of extensions (ransomware often creates new and therefore suspicious extensions: .qqq, .lockbit, etc.),
- Writing entropy (the more random the files written, the more likely it is to be encryption).
Detecting these abnormal behaviors makes it possible to identify potential attacks even before any intervention on Canary files.
But some ransomware goes further than encryption, with attackers strategizing to eliminate defenses before taking action. As mentioned above, they adapt to avoid detection and even disable cybersecurity tools – and for this reason, HarfangLab also provides self-protection for its agent.
Facing ransomware: protecting protection tools
Certain ransomware families, such as BlackCat and Akira, attempt to execute tampering scripts to disable EDRs.
Preserving system integrity
HarfangLab protects itself at the kernel level by preventing malicious processes from disabling it or modifying its behavior. As a result, even when actions are taken by accounts with high privileges, the core protection remains active.
Protecting communication between agent and manager
To deploy ransomware, attackers may attempt to isolate the agent from its manager by blocking its network communications. HarfangLab is able to detect this filtering and can automatically remove the rule causing it at the firewall, local proxy, etc. The SOC thus retains its remote response capabilities in the face of an ongoing attack.
Against ransomware: beyond tools, best practices, and human intelligence
Ransomware not only affects technical operations, it also poses a threat with potential geopolitical and human implications. Without a solid foundation and essential cybersecurity best practices in place, protection will remain incomplete even with the best technologies. Effective protection therefore lies in the synergy between the tools and the humans who operate them.
Behind every successful compromise, we generally find:
- Information system users not sufficiently aware of cybersecurity issues, who click on suspicious files, share passwords in plain text, etc.
- Vulnerable, outdated, or obsolete equipment, servers, or operating systems
- Network architectures not segmented or only minimally segmented, enabling attackers to move easily once they have penetrated the information system
- Insufficient protection of equipment with overly broad rights, open ports, or remote control tools
The expert’s view
“Ransomware has changed. The threat goes far beyond technology and takes the form of coordinated, industrialized, often automated operations, sometimes underpinned by geopolitical issues.
That’s why a single tool, however powerful, is not enough to deal with it. You need a responsive SOC, a properly configured SIEM, cyber hygiene, and solid governance.
The answer lies as much in the technological building blocks as in the ability to devise a defensive strategy specific to each SOC, each context, and each organization.
Léna Jakubowicz, Presales Lead – HarfangLab
How can you protect your workspace effectively?
Find out everything our platform can do for you: