TYPES OF CYBER ATTACKS
And what to do to strengthen security
Cyberattacks can be carried out by different types of attackers, with more or less sophisticated techniques, resulting in more or less critical damage for an organization’s information system.
Indeed, a security incident can result in data loss, intellectual property theft, disruption of service involving operating losses and the cost of restoring operational conditions, reputational damage, or the attackers may demand the payment of a ransom.
To begin with, let’s look at the different types of attacker. An incident may involve :
- cybercrime, with attacks that are generally not technically sophisticated, such as extorting money (particularly via ransomware or scams), making a service unavailable, etc.,
- hacktivism, or cyberactivism, in the form of high-powered hacking operations (website defacement, Distributed Denial of Service or DDoS attacks, etc.), aimed at expressing political disagreement or influencing political or societal change,
- more sophisticated advanced persistent threats, or APTs, consisting of infiltrating information systems for espionage or data exfiltration, etc.
Any organization can be targeted by one or more of these types of attackers, whatever its sector of activity or size.
However, it is important to bear in mind that, in practice, both APTs and cybercriminals seek to rationalize their efforts.
APT actors are less likely to attempt to attack a SMB, unless they have a very good reason to do so, and cybercriminals are more likely to need solvent victims who can pay a ransom.
Let’s take a look at the different categories of common attacks, what they involve, the level of risk, and how to protect against them.
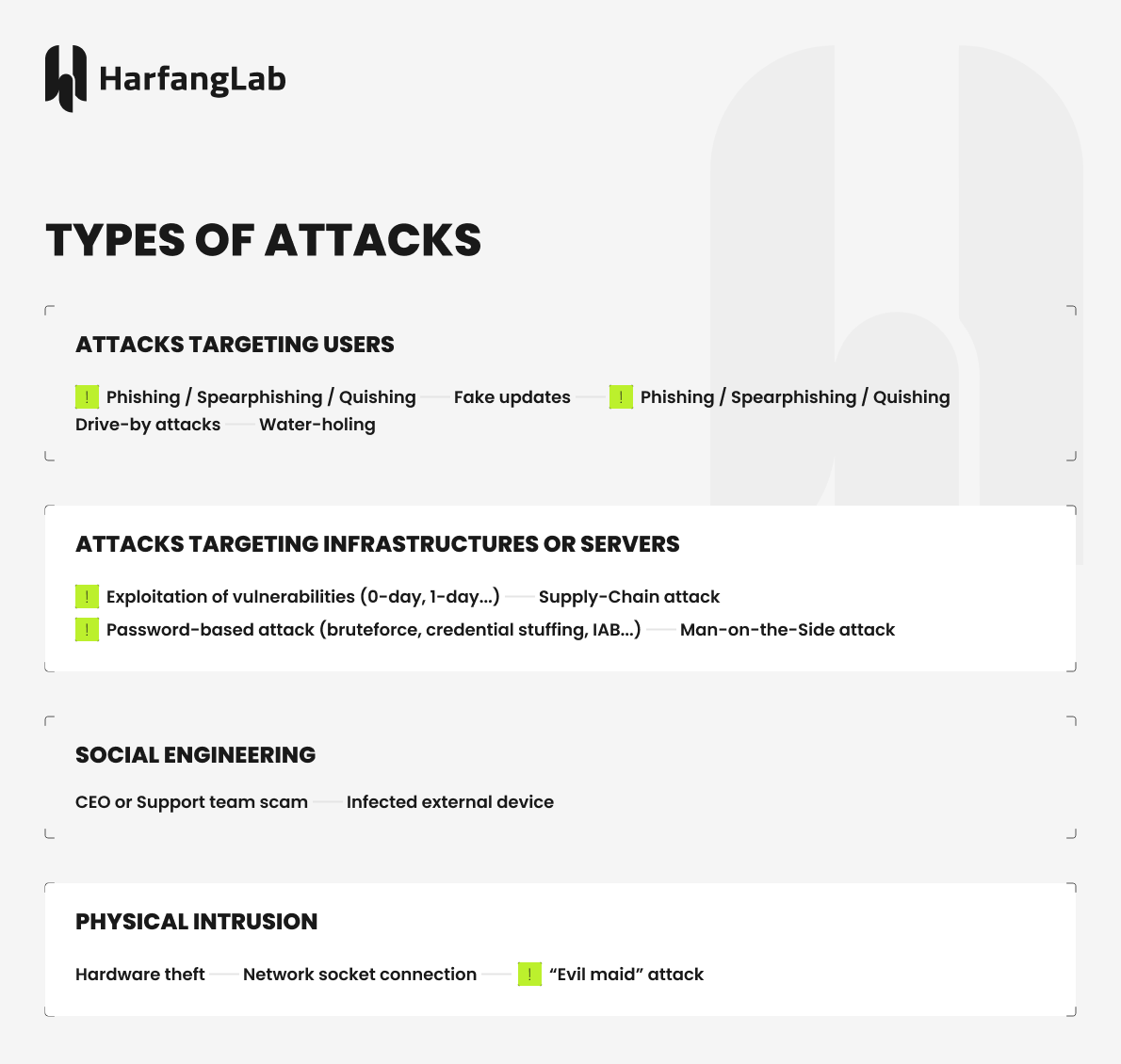
Common cyberattacks targeting users
Phishing / Spearphishing / Quishing
Sending an email containing a link, or providing a QR code, leading to a fraudulent site aimed at recovering identifiers or personal data.
- Tools for protection: spam filter, emails scans, awareness.
Cybersecurity risk level: endemic, depending on the attacker’s expected gain and the resources required to carry out the attack. Phishing emails are used on a massive scale by all types of attackers.
Malicious file attachments in email
Office or PDF documents attached to an email containing malicious code, macros or scripts that are executed when the file is opened or following a user action, or a document that exploits a software vulnerability in the e-reader.
- Tools for protection: antivirus, e-reader configuration (disable Macros globally, or block JavaScript in the PDF e-reader), awareness.
Cybersecurity risk level: very high. It’s a very popular intrusion vector, despite the presence of countermeasures on most email hosts. Every company has employees whose main task is to process files from unknown senders (invoices, CVs, complaints, etc.), making this kind of threat particularly effective.
Fake updates
Messages or alerts encouraging the installation of fraudulent software updates to infect the user’s equipment.
- Tools for protection: antivirus, awareness.
Cybersecurity risk level: medium. The misuse of advertising networks enables attackers to widely distribute fake installers and updates for legitimate applications. Note: the less experienced users are, the greater the risk.
Malicious applications installation
From the default app store, or from third-party app stores, attackers can imitate the appearance of a legitimate application to distribute a malicious one, or create one ad hoc to infect a mobile device.
- Tools for protection: awareness.
Cybersecurity risk level: low. The misuse of advertising networks can exacerbate the problem, but the security model for mobile devices reduces the impact of installing malicious applications (theft of personal data, etc.).
“Drive-by” attacks
Infection via the injection of malicious elements on a website (e.g., code exploiting a vulnerability in the visitor’s browser), without the user actually downloading or installing a file or executable. The link is sometimes transmitted to the victim by email, or via a messaging application.
- Tools for protection: browser updates, antivirus, NoScript
Cybersecurity risk level: low for the public, high for any entity or individual likely to attract the unfavorable attention of an intelligence service. Web browser vulnerabilities are generally too costly for cybercriminals to afford, but this particularly dangerous class of attack is the royal road for intrusions into the mobile world.
Water-holing
Water-holing consists in taking advantage of knowledge of victims’ habits to infect their device. For example, the attacker can identify one of the sites that the target regularly visits, enter it and maliciously modify it to exploit a browser flaw, offer fake updates…
- Tools for protection: awareness
Cybersecurity risk level: low. Sophisticated technique requiring behavioral information about victims. Seen mainly in the context of highly targeted attacks, or those aimed at specific populations (minorities, criminal networks…).
Common cyberattacks targeting infrastructures and servers
Exploitation of vulnerabilities
Exploitation of vulnerabilities in an application, for which a publisher has not yet implemented a patch (0-day, 1-day vulnerability…), to divert its use, render it inoperative, proceed to code injection, etc.
- Tools for protection: keeping applications up to date (1-day), anti-virus to protect against 0-day vulnerabilities, and EDR to detect intrusions.
Cybersecurity risk level: very high. Even with a good update policy, software vulnerabilities can be exploited on a massive scale as soon as 12 hours after they are disclosed.
Password-based attacks
Attempts to access services via legitimate user accounts, using brute-force attack techniques (password guessing until the right one is found), credential stuffing (reuse of leaked credentials), purchase of credentials from an IAB (Initial Access Broker), or fraudulent installation of a keylogger.
- Tools for protection: password manager and digital hygiene (strong, different passwords for each service).
Cybersecurity risk level: high. The level of digital hygiene when it comes to passwords remains generally low, and regular data leaks enable attackers to build up huge databases of username/password pairs.
Supply Chain attacks
A so-called “supply-chain” attack consists of stealthily injecting malicious code into a product, or compromising protocols, equipment or network components.
Cybersecurity risk level: medium. Although frequent, they are less likely to target non-strategic entities. Nevertheless, for software publishers, the risk must be considered high, as the possibility of their product being hijacked by an attack must be taken into account (particularly if they have prestigious clients).
Man-on-the-Side attacks
A “Man-on-the-Side” (MOTS) attack consists in a response injection from one of the two parties to a communication between them before the other has time to do so. This type of attack requires active interception capabilities.
Cybersecurity risk level: low. The number of actors capable of carrying out such an attack is extremely limited… but it is virtually impossible for most companies to protect themselves.
Common cyberattacks via social engineering
CEO or Support team scams
Contact by phone call, phone message or email to induce a mistake: transmitting sensitive data, modifying access rights, transferring money, etc. For example, by impersonating a manager or a member of the organization’s technical team.
- Tools for protection: specific awareness on this topic.
Cybersecurity risk level: although the attack vector is said to be highly efficient, it is difficult to quantify its prevalence.
Infected extrernal device
Delivery of infected hardware, such as USB key, external hard drive or any other device that can be plugged into a user’s computer. It may contain a malicious file that the victim clicks on out of curiosity, or even identifies to the system and sends commands to the machine in the form of keystrokes (e.g. Rubber Ducky from Hak5).
- Tools for protection: antivirus, awareness.
Cybersecurity risk level: low. This type of attack requires the physical presence of the attacker and therefore implies that the victim has been specifically targeted.
Common physical intrusions
Hardware theft
Attackers can break into an organization’s premises, or take advantage of a user’s inattention in a public place to steal their computer, hard disk, telephone, etc.
- Tools for protection: securing access to premises, awareness.
Cybersecurity risk level: low. This type of attack requires the physical presence of the attacker and therefore implies that the victim has been specifically targeted.
Network socket connection
Unauthorized connection to an organization’s network, by surreptitiously connecting to an unattended network socket on the premises.
- Tools for protection: avoid sharing unused sockets, secure access to premises.
Cybersecurity risk level: low. This type of attack requires the physical presence of the attacker and therefore implies that the victim has been specifically targeted.
“Evil maid” attacks
Attack consisting of accessing a machine in the absence of the owner (e.g. hotel room, hence the name) and copying data from the hard disk, even if this means physically removing it from the computer. An alternative is to install a bootkit virus, which will be executed the next time the computer is booted.
- Tools for protection: BIOS password, SecureBoot, FDE (Full Disk Encryption).
Cybersecurity Cybersecurity risk level: very high on the move, and at border crossings.