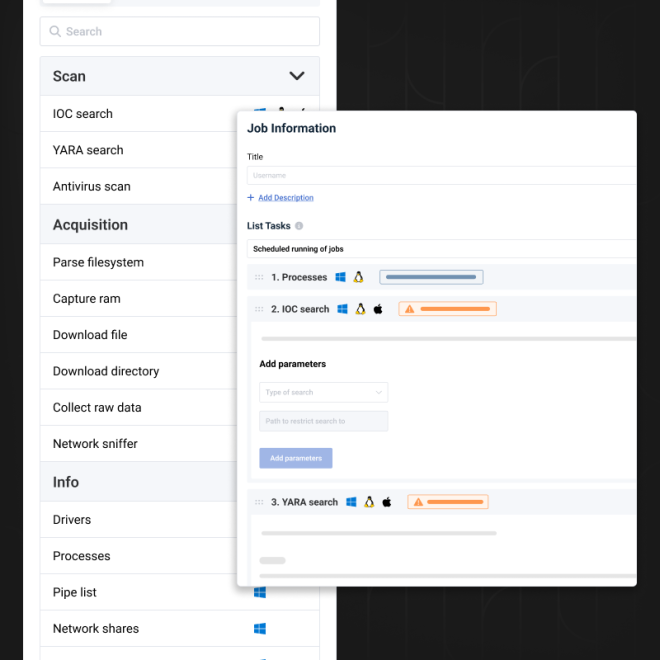
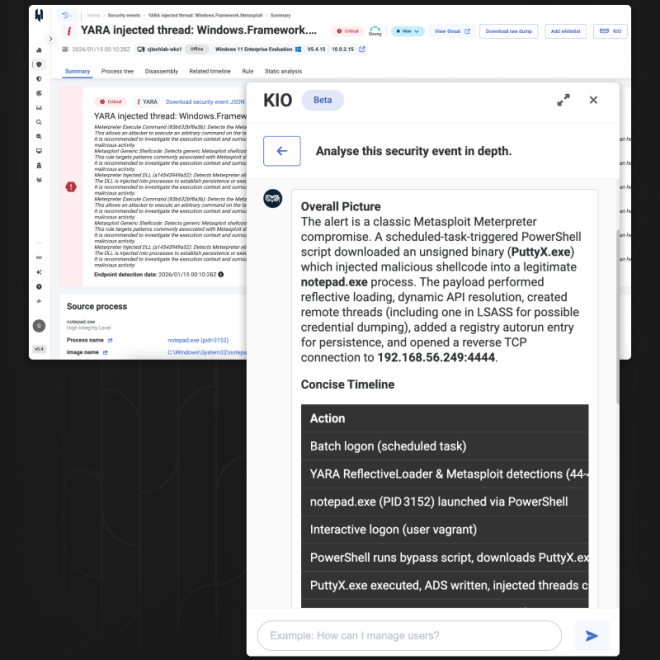
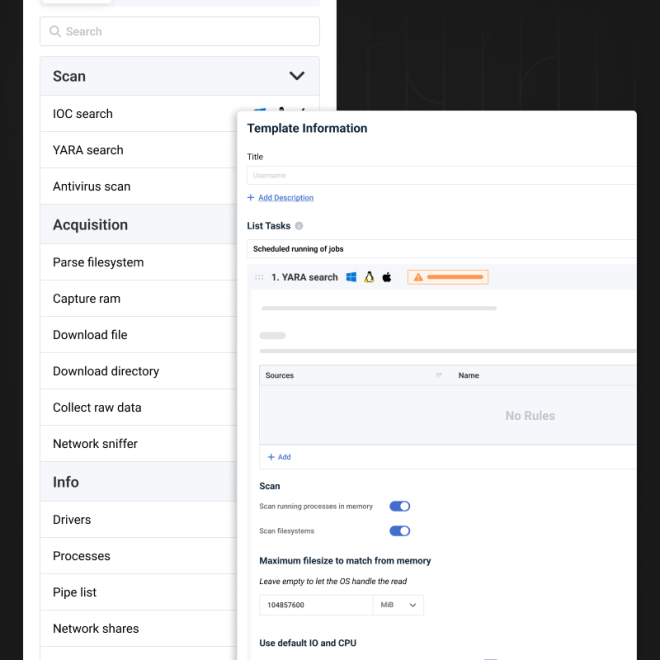
In addition to all available telemetry, collect data and artifacts on endpoints to run accurate and effective investigations to qualify threats (cybercrime, advanced persistent attacks) and implement remediation measures.
Launch jobs to perform actions on one or more endpoints, and analyze the results directly from your console:
- RAM capture
- Running processes capture
- Driver information retrieval
- Detailed endpoints structure visualization
- Endpoint’s network communications exploration
- Threat persistence detection (registries, scheduled tasks, startup files, etc.)